Security Services Addendum
- INTRODUCTION
The Security Services offering by Corporate Network Solutions provides Clients with a scalable information security solution, capable of detecting and notifying on potential security threats against a Client’s environment. This proprietary set of systems and processes utilizes state of the art hardware, software, and security industry professionals to observe and monitor Client network(s), endpoint(s), and other related events to detect anomalous actions and security threats. - AGREEMENT
This Security Services Addendum (“SSA”) sets forth the specific terms and conditions under which Corporate Network Solutions shall supply Information Security Services to Client. The Master Service Agreement entered into between Corporate Network Solutions and Client, fully incorporates the terms herein and provides that this SSA, and Client’s execution of the Master Services Agreement constitutes acceptance of the terms and conditions stated herein. Capitalized terms used but not defined herein shall have the meanings set forth in the Master Services Agreement. The Initial Term length for this Service is set forth on the applicable Service Order Form (“SOF”), executed by Corporate Network Solutions and Client, referring to these Services. As referred to herein, “Agreement” means this Security Services Addendum, together with the MSA and all policies and addenda that are incorporated herein by reference, including the Statement of Work (SOW), Responsibility Matrix (“RM”), Service Level Agreement (SLA), Acceptable Use Policy (“AUP”), and Privacy Policy (“PP”). This Agreement sets forth the terms and conditions that apply to the Security Services Addendum. - GENERAL
Corporate Network Solutions will examine the Client’s current computer networking platform, its hosting, and data security requirements to the extent Client has provided Corporate Network Solutions access, and confirms that the agreed upon Service(s) may interact and operate with the Client’s platform and provide a secure environment in accordance with the specifications, and in accordance with industry standards set forth in the agreed upon Statement of Work (SOW).If the agreement between Corporate Network Solutions and the Client is terminated or expires, Client shall have the option to either renew the agreement or replace the Corporate Network Solutions Security Services with a third-party provider of its choosing. Upon request, Corporate Network Solutions shall undertake commercially reasonable efforts to transition Client to the new provider as quickly, economically and efficiently as possible and if possible, will do so in a way that provides the most seamless and secure transition with minimal business interruptions to Client.
-
SERVICES AND FEATURES
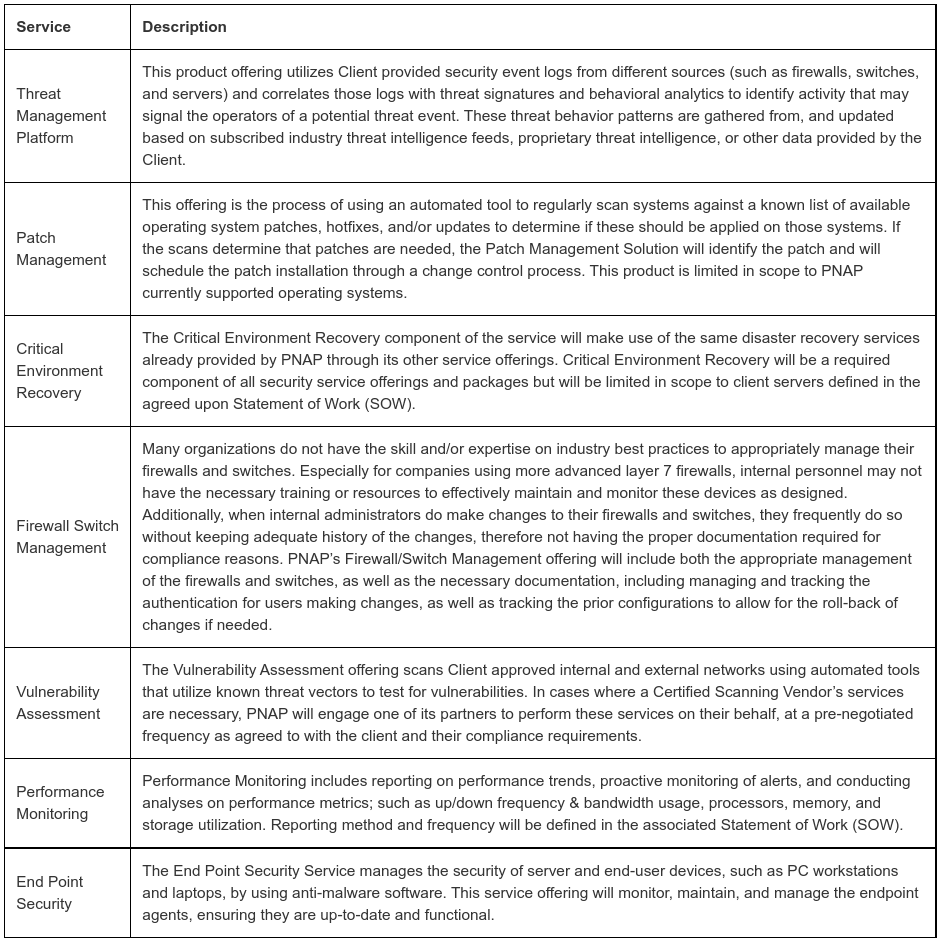
- BEST PRACTICES
Corporate Network Solutions shall implement the following best practices with regard to development and deployment of the Products and Services. Corporate Network Solutions shall maintain appropriate systems security for the Corporate Network Solutions’s Service in accordance with commercially reasonable industry standards and practices designed to protect all data and information provided by or on behalf of Client that is input into, displayed on or processed by the Corporate Network Solutions’s Service and all output therefrom (“Client Data”) from theft, unauthorized disclosure and unauthorized access. Such systems security includes, among other things: (1) implementation of application vulnerability tests and mitigation processes; (2) direct all Corporate Network Solutions-Client electronic communications via a secure web portal, a secure file share, or encrypted email; and (3) the following safeguards:- Authentication
- All access is authenticated, communication secured using industry best practices, and logged.
- Systems identity is tied to an individual user by the use of credentials and by a second factor authentication mechanism.
- Reasonable authentication controls that conform to industry recognized standards are provided.
- Authorization
- Ensure that authorized users are only allowed to perform actions within their privilege level.
- Control access to protected resources based upon role or privilege level.
- Mitigate and defend against privilege escalation attacks as feasible, to available technology standards and best practices.
- Password and Account Management
- Passwords conform to best practices, including:
- Encrypting passwords using “hashing” and “salting” techniques.
- Enforcing password complexity.
- Limiting failed attempts before account lockout.
- Not allowing storage and transmittal of passwords in clear text.
- Password reset does not send credentials.
- Where appropriate, Corporate Network Solutions shall securely log (with time and date) commands requiring additional privileges to enable a complete audit trail of activities.
- Passwords conform to best practices, including:
- Data Security
- Data at Rest
- Client Data is encrypted using industry best practices.
- Backups of Client Data have the same controls as production data.
- Data in Transit
- Client Data in transit to or from Client will be encrypted (e.g., SSL, VPN, SFTP, certificate-based authentication).
- Client Data sent over browser should use SSLv3 or better.
- Data at Rest
- Multi-Tenancy
- In a multi-tenant environment, Corporate Network Solutions shall provide appropriate security controls and robust cryptographic methods to protect and isolate Client Data from other tenants.
- Administrative Access and Environmental Segregation
- Applying Principle of Least Privilege: Proper controls should be in place to ensure that access is limited to personnel who must see Client Data in order to fulfill their job functions.
- Where possible, confidential data should be masked with one-way hashing algorithms.
- Client Data should not be replicated to non-production environments.
- Threat Management
- Intrusion Detection
Corporate Network Solutions shall implement and maintain an intrusion detection monitoring process at the network and host level to protect Corporate Network Solutions Services and to detect unwanted or hostile network traffic. Corporate Network Solutions shall update its intrusion detection software continuously, on a scheduled basis following the availability of updates by the chosen software provider. Corporate Network Solutions shall implement measures to ensure that Corporate Network Solutions is alerted when the system or service detects unusual or malicious activity. Corporate Network Solutions shall notify Client within twenty four (24) hours of any significant intrusion that involves a breach of customer’s data. - Penetration Tests
Corporate Network Solutions shall conduct penetration tests at least once per year on its Client-wide computing environment through a 3rd party Qualified Security Assessor (QSA), and appropriately dispose of the risks identified. Due to the high-risk nature of these reports, the reports and findings will not be publicly disclosed, or made available for client inspection. Corporate Network Solutions will however make available upon request, a letter from the QSA of satisfactory disposition of identified threat concerns. Clients will not be authorized to conduct vulnerability scans, assessments, or penetration tests against the Corporate Network Solutions service infrastructure. - Infrastructure Security
Corporate Network Solutions shall configure the infrastructure (e.g., servers and network devices) and platforms (e.g., OS and web servers) to be secure following these best practices:- Audit Logging: Client authorizes Corporate Network Solutions to collect, use, store, transfer, monitor and otherwise process logs from all systems subscribed to Corporate Network Solutions’s Service. These log types include, but is not limited to, security logs, web server logs, application logs, system logs and network event logs. Corporate Network Solutions monitors its networks 24/7 using the latest SIEM and behavioral analytics technologies. The Client acknowledges that these logs can contain source and destination IP addresses, user accounts used, bad passwords attempted, click and screen entries, and other personally identifiable data elements.
- Duplicate copies of these logs will be maintained, and an offsite archival copy will reduce risk of loss due to tampering.
- Network Security
- Corporate Network Solutions shall comply with industry standards, separating perimeter networks from endpoints hosted in the private network using industry standard firewalls or micro-segmentation techniques based on Software Defined Networking technologies. Corporate Network Solutions shall update and maintain its infrastructure using an industry standard maintenance and change control methodology.
- Corporate Network Solutions shall monitor and test its perimeter devices on a regular basis, and, if deficiencies are discovered, Corporate Network Solutions shall promptly troubleshoot and remediate these deficiencies.
- Vulnerability Management
In addition to the third-party vulnerability assessments described above, Corporate Network Solutions shall implement commercially reasonable processes designed to protect Client Data from system vulnerabilities, including:- Perimeter Scanning: Corporate Network Solutions shall perform perimeter scanning through the use of embedded sensors within Corporate Network Solutions’s infrastructure providing information to our centralized SIEM tool.
- Internal Infrastructure Scanning: Corporate Network Solutions shall perform internal infrastructure scanning through the use of embedded sensors within Corporate Network Solutions’s infrastructure providing information to our centralized SIEM tool.
- Malware Scanning: Where possible Corporate Network Solutions utilizes an advanced behavior and signature based anti-virus/anti-malware (APT) tool, along with application whitelisting techniques to protect its infrastructure from the threat of unauthorized malicious software.
- Secure Configuration
Corporate Network Solutions utilizes an industry standard methodology for platform hardening and secure configuration, in order to reduce attack scope and surface. Through the use of micro-segmentation techniques, lateral communication is further restricted to known communication pairs and patterns.
- Intrusion Detection
- Security Procedures
- Incident Response
Corporate Network Solutions shall maintain security incident management policies and procedures, including detailed security incident escalation procedures. In the event of a breach of Corporate Network Solutions’s security or confidentiality obligations, impacting a client’s environment or data, Corporate Network Solutions agrees to notify affected Client(s) by telephone and email of such an event within twenty-four (24) hours of discovery. Corporate Network Solutions will also promptly perform an investigation into the breach, take appropriate remedial measures, and assign a Single-Point-of-Contact (SPoC). This SPoC or their designee, will be available for security questions or concerns twenty-four (24) hours per day, seven (7) days per week, during the scope of Corporate Network Solutions’s investigation. - Patch Management
Corporate Network Solutions shall use a patch management process and tool set to keep all servers up to date with appropriate security and feature patches. - Documented Remediation Process
Corporate Network Solutions shall use a documented remediation process designed to timely address all identified threats and vulnerabilities with respect to the Corporate Network Solutions Service.
- Incident Response
- Employee Termination Procedures
- Corporate Network Solutions shall promptly terminate all credentials and access to privileged password facilities, such as Identity and Access Management Systems, upon termination of employment.
- Governance
- Security Policy
Corporate Network Solutions shall maintain a written information security policy that is approved annually by Corporate Network Solutions and published and communicated to all Corporate Network Solutions employees and relevant third parties. Corporate Network Solutions shall maintain a dedicated security and compliance function to design, maintain and operate security in support of its “trust platform” in line with industry standards. This function shall focus on system integrity, risk acceptance, risk analysis and assessment, risk evaluation, risk management and treatment statements of applicability and Corporate Network Solutions management. - Security Training
Corporate Network Solutions shall ensure, at no expense to Client, that all Corporate Network Solutions employees and Clients complete relevant training required to operationalize the procedures and practices outlined herein, including security awareness training, on at least an annual basis. - Security Reviews
Corporate Network Solutions and Client may meet at least once annually to discuss: (1) the effectiveness of the Corporate Network Solutions’s security platform; and (2) any updates, patches, fixes, innovations or other improvements made to electronic data security by other commercial providers or for other customers of Corporate Network Solutions that Corporate Network Solutions or Client believe will improve the effectiveness of the Corporate Network Solutions’s security platform for Client. - Third-Party Audits and Compliance Standards
- Corporate Network Solutions shall provide Client with a copy of SOC2 or similar audit results, in no more than thirty (30) days after Corporate Network Solutions receives the results or reports. Client has the right to, or to engage a third party on its behalf to, visit Corporate Network Solutions’s offices up to four (4) times per calendar year in order to conduct due diligence and auditing procedures on Corporate Network Solutions’s business operations related to the Corporate Network Solutions’s Service in terms of technical infrastructure, system interaction, organization, quality, quality control, personnel involved with services for Client, and general resources in terms of skills and personnel.
- Corporate Network Solutions will furnish evidence of a successful SSAE No. 18 audit upon Client request to the extent permitted by law and subject to applicable regulatory restrictions and confidentiality obligations. Corporate Network Solutions must verify that the audit certifies all infrastructure and applications that support and deliver services to Client Data.
- PCI-DSS Compliance
Corporate Network Solutions shall maintain policies, practices and procedures sufficient to comply with the Payment Card Industry Data Security Standard, as the same may be amended from time to time, with respect to the Corporate Network Solutions’s Service. - Vulnerability Assessments
Corporate Network Solutions shall conduct application vulnerability assessments at least annually. These assessments will be conducted with a 3rd party Qualified Security Assessor (QSA). Due to the high-risk nature of these reports, the reports and findings will not be publicly disclosed, or made available for client inspection. Corporate Network Solutions will however make available upon request, a letter from the QSA of satisfactory disposition of identified threat concerns. Clients will not be authorized to conduct vulnerability scans, assessments, or penetration tests against the Corporate Network Solutions application platforms.
- Security Policy
- Physical Security
Corporate Network Solutions shall limit access to its facilities utilized in performing the Corporate Network Solutions’s Service to employees and authorized visitors using commercially reasonable industry standard physical security methods. At a minimum, such methods shall include visitor sign-ins, restricted access key cards and locks for employees; limited access to server rooms and archival backups; and burglar/intrusion alarm systems. - Business Continuity
Corporate Network Solutions shall have a business continuity plan in place for the restoration of critical processes and operations of the Corporate Network Solutions’s Service at the location(s) from which the Corporate Network Solutions’s Service is provided. Corporate Network Solutions shall also have an annually tested plan in place to assist Corporate Network Solutions in reacting to a disaster in a planned and tested manner. Corporate Network Solutions shall provide Client with a copy of its then-current plan promptly following Client’s written request for same. - Corporate Network Solutions Internal Systems Backup Management
- Corporate Network Solutions shall perform full backups of internal systems and database(s) containing Client Data no less than once per day without interruption of the Corporate Network Solutions Service. Corporate Network Solutions shall also provide off-site archival storage on no less than a weekly basis of all backups of the internal systems and database(s) containing Client Data on secure server(s) or other commercially acceptable secure media. Such data backups will be encrypted, sent off-site to a secure location each business day and stored/retained for seven (7) years.
- In order to recover from a Datacenter failure Incident, the required backed-up data will be replicated over at least two (2) geographically dispersed data centers at any point in time. Backup snapshots may be periodically sent to another data center. Data retention for an in-datacenter failure Incident will utilize twenty-four (24) hourly snapshots, fourteen (14) daily backups and three (3) monthly backups. This backup policy is designed to support both a partial or full recovery of the system expediently.
- Right to Audit
Client has the right to, or to engage a third party on its behalf to, at its own expense, visit Corporate Network Solutions’s offices once per calendar year in order to conduct due diligence and auditing procedures on Corporate Network Solutions’s business operations related to the Corporate Network Solutions’s Service in terms of technical infrastructure, systems interaction, organization, quality, quality control, personnel involved with services for customers, and general resources in terms of skills and personnel. Understanding the proprietary and intellectual property nature of this access, Client agrees to execute and abide by a Non-Disclosure Agreement, and limit the documentation or removal of this information from Corporate Network Solutionss premises.
- Authentication
- CLIENT RESPONSIBILITIES
Client shall document and promptly report all errors or malfunctions of a system covered under this agreement to Corporate Network Solutions. Corporate Network Solutions shall provide all necessary spare parts and/or other hardware to maintain equipment owned by it necessary to the fulfillment of any service under this Schedule.Client shall not use anything whether tangible or intangible which is appurtenant to and/or provided by this agreement for any unlawful purpose or for any purpose which is prohibited by Corporate Network Solutions’s Network Abuse Policy and/or Acceptable Use Policy as is posted on its website.
Customer acknowledges that Corporate Network Solutions performance and delivery of the Services are contingent upon: (A) Customer providing safe and hazard-free access to its personnel, facilities, equipment, hardware, network and information, and (B) Customer’s timely decision-making and provision of timely, accurate and complete information and reasonable assistance, including, granting of approvals or permissions, as (A) and (B) are deemed reasonably necessary and reasonably requested for Corporate Network Solutions to perform, deliver and/or implement the Services. Customer will promptly obtain and provide to Corporate Network Solutions any required licenses, approvals or consents necessary for Corporate Network Solutions’s performance of the Services. Corporate Network Solutions will be excused from its failure to perform its obligations under this Addendum to the extent such failure is caused solely by Customer’s delay in performing or failure to perform its responsibilities under this MSA and/or the Service Order/SOW.
- STATEMENT OF WORK; RESPONSIBILITY MATRIX
A Statement of Work (“SOW”) and Responsibility Matrix (“RM”) shall be used to specify the specific duties, scope, locations, deliverables, standards, activities, and general requirements for any Information Security Service offered by Corporate Network Solutions to a Client. - SERVICE LEVEL AGREEMENT (SLA)
The following Corporate Network Solutions Service Level Agreement (“SLA”) is a policy governing the use of the Corporate Network Solutions Security Services under the terms of the Master Service Agreement (the “MSA”) between Corporate Network Solutions, LLC., and Clients of Corporate Network Solutions. Unless otherwise provided herein, this SLA is subject to the terms of the MSA and capitalized terms will have the meaning specified in the Agreement. We reserve the right to change the terms of this SLA in accordance with the MSA.
Service Types, Priority, and Response Times
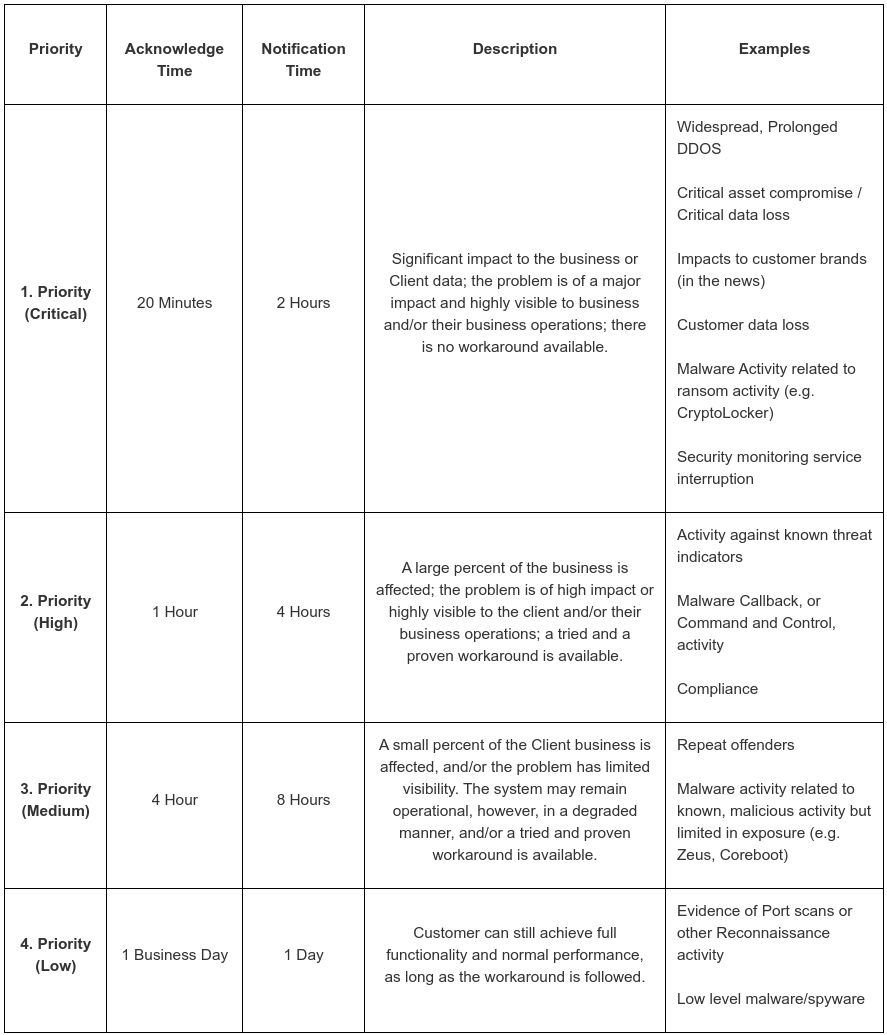
- Service Commitment
Corporate Network Solutions will use commercially reasonable efforts to make Security Services available with a Monthly Uptime Percentage of 100%, excluding scheduled and pre-acknowledged maintenance periods where alternative procedures are in place for continuous monitoring. As described in section A: Service Types, Priority, and Response Times, Corporate Network Solutions, on receipt of an alert, will “acknowledge” (either through email or telephonically), in the described timeframes, the impact of the incident and the actions that should be taken to mitigate the concern.
In the event Corporate Network Solutions does not meet the Monthly Uptime Percentage commitment, Client will be eligible to receive a Service Credit as described below. - Service Credits
If the Monthly Uptime Percentage for a Client drops below 100% during a Service Month, that Client is eligible to receive one (1) 10% Service Credit, for every thirty (30) minute period that Security Services was Unavailable, up to a maximum amount equal to one full month’s billing. For the purposes of determining Service Credits, Client will only be eligible for Service Credits related to the unavailability of:- InfraSentry: Monitor Threat Detection Service
- InfraSentry: Sophos related “Advanced Persistent Threat” tools
Whichever Service was least available during the Service month, Corporate Network Solutions will apply any Service Credits only against future payments otherwise due from Client, provided that:
- Corporate Network Solutions may issue the Service Credit to the Client account for the Service Month in which the Unavailability occurred, and
- Client is current with all payment obligations set forth in the Agreement.
Service Credits shall not entitle Client to any refund or other payment from Corporate Network Solutions. Service Credits may not be transferred or applied to any other account. Unless otherwise provided in the Agreement, Service Credits are Client’s sole and exclusive remedy for any unavailability or non-performance of Services.
- Credit Request and Payment Procedures
To receive a Service Credit, Client must submit a request by sending an e-mail message to noc@Corporate Network Solutions.com. To be eligible, the credit request must:- Include SLA Service Credit Claim in the subject of the e-mail message;
- Include, in the body of the e-mail, Client’s Organization name, or Client ID, along with the dates, times, and length of each Unavailability Period that Client claims to have experienced;
- Include any documentation that corroborates Client’s claimed Unavailability; and
- Be received by Corporate Network Solutions within thirty (30) calendar days of the last day reported in the Unavailability claim.
If the Monthly Uptime Percentage of such request is confirmed by Corporate Network Solutions and is less than 100% for the Service Month, then Corporate Network Solutions will issue the Service Credit to Client within one Service Month following the month in which the request has been confirmed. Client’s failure to provide the request and other information as required above will disqualify Client from receiving a Service Credit. Corporate Network Solutions’s data and records will be the sole factor for validating claims due to Unavailability.
- Exclusions
The Service Commitment does not apply to any unavailability, suspension or termination of Security Services, or any other performance issues:- That result from Service Suspensions described in the following sections of the Agreement: Term and Termination, and Default Events and Remedies;
- Caused by factors outside of the reasonable control of Corporate Network Solutions, including any force majeure event or Internet access or related problems beyond the Corporate Network Solutions Network Demarcation Point;
- That result from any actions or inactions of Client or any third party;
- That result from Client equipment, software or other technology and/or third party equipment, software or other technology (other than third party equipment within Corporate Network Solutions’s direct control);
- That result from failures of individual functions, features, infrastructure, and network connectivity Unavailability; or
- Arising from Corporate Network Solutions’s suspension and termination of Client’s right to use Security Services in accordance with the Agreement.
If availability is impacted by factors other than those explicitly listed in this agreement, Corporate Network Solutions may issue a Service Credit considering such factors in our sole discretion.
- Disclaimer
If Corporate Network Solutions misses the SLA goal because of problems with Client’s behavior or the performance or failure of Client’s equipment, facilities, or applications, Corporate Network Solutions can’t give Client credit. Additionally, extenuating circumstances beyond Corporate Network Solutions’s reasonable control such as (without limitation) acts of any governmental body, acts of terrorism, war, insurrection, sabotage, embargo, fire, flood, strike or other labor disturbance, interruption of or delay in transportation, unavailability of interruption or delay in telecommunications or third party services (including DNS propagation), failure of third party software or hardware or inability to obtain raw materials, supplies, or power used in or equipment needed for provision of Client’s services could cause some hang-ups that Corporate Network Solutions cannot be liable for.
- DISCLAIMERS
- No Product Warranty
Corporate Network Solutions makes no express or implied warranties of product merchantability or fitness for any particular purpose. While all services are designed to be resilient, it is up to the Client to plan for disasters and it is always recommended to keep an off-site backup of critical data in event of critical failure or disaster. - Disclaimer of Warranty
Corporate Network Solutions WILL NOT BE LIABLE FOR ANY LOSS OR DAMAGE CAUSED BY A DISTRIBUTED DENIAL-OF-SERVICE ATTACK, VIRUSES OR OTHER TECHNOLOGICALLY HARMFUL MATERIAL THAT MAY INFECT YOUR COMPUTER EQUIPMENT, COMPUTER PROGRAMS, DATA NETWORK OR OTHER PROPRIETARY MATERIAL RESULTING FROM YOUR USE OF THE SERVICES, Corporate Network Solutions’S WEBSITE OR THE SERVICE OR ITEMS PURCHASED OR OBTAINED THROUGH THE WEBSITE OR THE SERVICE OR TO YOUR DOWNLOADING OF ANY MATERIAL POSTED ON IT, OR ON ANY WEBSITE LINKED TO IT. NEITHER Corporate Network Solutions NOR ANY PERSON ASSOCIATED WITH Corporate Network Solutions MAKES ANY WARRANTY OR REPRESENTATION TO ANY USER WITH RESPECT TO THE COMPLETENESS, SECURITY, RELIABILITY, QUALITY, FUNCTIONALITY OR AVAILABILITY OF THE SERVICES. WITHOUT LIMITING THE FOREGOING, NEITHER Corporate Network Solutions NOR ANYONE ASSOCIATED WITH Corporate Network Solutions REPRESENTS OR WARRANTS THAT THE SERVICE WILL BE RELIABLE, ERROR-FREE, INTRUSION PROOF OR UNINTERRUPTED, THAT DEFECTS WILL BE CORRECTED, FREE OF VIRUSES OR OTHER HARMFUL COMPONENTS OR THAT THE SERVICES WILL OTHERWISE MEET THE NEEDS OR EXPECTATIONS OF CLIENTOR ANY USER. EXCEPT FOR THE WARRANTY SET FOR ABOVE, Corporate Network Solutions PROVIDES THE SERVICE, AND ALL ON AN “AS IS” AND “AS AVAILABLE” BASIS, WITHOUT ANY WARRANTIES. Corporate Network Solutions HEREBY DISCLAIMS ALL WARRANTIES OF ANY KIND, WHETHER EXPRESS OR IMPLIED, STATUTORY OR OTHERWISE, INCLUDING BUT NOT LIMITED TO ANY WARRANTIES OF MERCHANTABILITY, NON-INFRINGEMENT AND FITNESS FOR PARTICULAR PURPOSE.
Corporate Network Solutions AGGREGATE LIABILITY (WHETHER IN CONTRACT, TORT OR OTHERWISE) FOR ALL CLAIMS OF LIABILITY ARISING OUT OF, OR IN CONNECTION WITH, THE AGREEMENT SHALL NOT EXCEED THE AMOUNTS PAID BY CLIENTFOR THE SERVICES GIVING RISE TO A CLAIM FOR LIABILITY. THE FOREGOING DOES NOT AFFECT ANY WARRANTIES WHICH CANNOT BE EXCLUDED OR LIMITED UNDER APPLICABLE LAW. THIS SECTION SHALL SURVIVE ANY EXPIRATION OR TERMINATION OF THE AGREEMENT.
IN NO EVENT WILL Corporate Network Solutions, ITS AFFILIATES OR THEIR LICENSORS, SERVICE PROVIDERS, EMPLOYEES, AGENTS, OFFICERS OR DIRECTORS BE LIABLE FOR DAMAGES OF ANY KIND, UNDER ANY LEGAL THEORY, ARISING OUT OF OR IN CONNECTION WITH YOUR USE, OR INABILITY TO USE, THE SERVICES OR ANY WEBSITES ASSOCIATED WITH IT, INCLUDING ANY DIRECT, INDIRECT, SPECIAL, INCIDENTAL, CONSEQUENTIAL OR PUNITIVE DAMAGES, INCLUDING BUT NOT LIMITED TO, PERSONAL INJURY, PAIN AND SUFFERING, EMOTIONAL DISTRESS, LOSS OF REVENUE, LOSS OF PROFITS, LOSS OF BUSINESS OR ANTICIPATED SAVINGS, LOSS OF USE, LOSS OF GOODWILL, LOSS OF DATA, AND WHETHER CAUSED BY TORT (INCLUDING NEGLIGENCE), BREACH OF CONTRACT OR OTHERWISE, EVEN IF FORESEEABLE. THE FOREGOING DOES NOT AFFECT ANY LIABILITY WHICH CANNOT BE EXCLUDED OR LIMITED UNDER APPLICABLE LAW. - Limitation on Time to File Claims
Any cause of action or claim You may have arising out of or relating to these terms of use, the service or the website must be commenced within one (1) year after the cause of action accrues, otherwise, such cause of action or claim is permanently barred. - Notice of Loss
Corporate Network Solutions is not liable for any loss or corruption of data. Clients are always encouraged to retain a copy of data. In the event of loss or destruction of or damage to Client data, Corporate Network Solutions will provide notification to Client via e-mail to an address provided by the Client. Client must ensure that the e-mail address is valid.
- No Product Warranty
- CONSENT
By entering this Agreement and by using the Services, Client consents to, and hereby agrees that Corporate Network Solutions may access Client’s networks and computer systems including the access to and use, disclosure, interception, transmission, receipt, analysis, processing, copying, editing, encryption, decryption, and storage of Client information and that of its employees, agents and those it authorizes to use the Services, whether encrypted or in clear text (“Client’s Information”) for the purpose of providing the Services, including, without limitation, analyzing Client’s network traffic, and for storage and retention of Client’s Information for future reference and analysis. Client represents and warrants that it complies with all applicable data collection and transfer laws and regulations of the countries in which it operates and that it has duly obtained all consents, permits or licenses, in writing or electronically that may be necessary under applicable laws from its employees, agents, and those it authorizes to use the Services in order to enable Corporate Network Solutions to provide the Services under the Agreement. Prior to using the Services, or at any other time reasonably determined by Corporate Network Solutions, Client will provide Corporate Network Solutions true and correct copies of such consents. - INDEMNITY
Client shall defend, indemnify and hold harmless the Corporate Network Solutions Indemnified Parties from and against any damages, orders, decrees, judgments, liabilities, claims, actions, lawsuits, costs and expenses (including, without limitation, costs of litigation and attorneys’ fees) (“Claims”) incurred by the Corporate Network Solutions Indemnified Parties or finally adjudicated against the Corporate Network Solutions Indemnified Parties arising out of or resulting from: (i) infringement of intellectual property rights, including, without limitation, copyright, trademark, trade secret, patent, and common law rights in connection with Client’s Information, networks, or computer systems; (ii) violation of applicable laws or policies by Client, including, without limitation in connection with Client Information, networks, or computer systems; (iii) failure by Client to secure all necessary consents, permits, and licenses, including without limitation, in connection with Customer’s Information, networks, or computer systems; (iv) breach of warranty by Client; (v) breach of this Agreement by Client; (vi) use of Services by Client or Client Affiliates; (vii) negligence, intentional misconduct or other wrongful acts or omissions by Customer; and (viii) Claims alleging that Corporate Network Solutions was not authorized to provide Services requested by Customer.
This Section states each party’s exclusive remedies for any third-party claim or action, and nothing in this Agreement or elsewhere will obligate either party to provide any greater indemnity to the other. - SUBCONTRACTING
Corporate Network Solutions may assign, subcontract or delegate in whole or in part this Agreement, or any rights, duties, obligations or liabilities under this Agreement, by operation of law or otherwise, provided that Corporate Network Solutions shall remain responsible for the performance of Services under this Agreement. Otherwise, neither party may assign this Agreement without the permission of the other party, which permission shall not be unreasonably withheld, conditioned or delayed. - CHARGES
The subsections of this section define the recurring and non-recurring charges and fees pursuant to this schedule.- MONTHLY RECURRING FEES
The Initial Monthly Recurring Charges are the initial monthly fees charged for this Schedule. This fee may be modified by mutual agreement of Client and Provider based on changes to the initial configurations, covered devices, or other similar environment variables. - NON-RECURRING SERVICE FEES
The non-recurring services and fees associated with this Schedule include but are not limited to any Out-of-Scope fees and/or the fees for any associated labor and other services provided under a Statement of Work or for the migration/installation/implementation of Client’s production environment from its current state to Provider’s Cloud/Hosting environment or for other purposes agreed to by Provider and Client, including, but not limited to, those defined in a Statement of Work as one time or non-recurring fees or services whether created at the time of or subsequent to the execution of this agreement. - INITIAL SETUP FEES
The initial setup fees and charges for this Schedule are the one-time non-recurring fees associated with the initial setup of Client’s services. This fee may be modified by mutual agreement of Client and Provider based on changes to the initial configurations, scope, covered devices or other similar environment variables. Initial Setup Fees do not include the charges for Data Migration. Data Migration Fees will be specified and covered under a separate Statement of Work or Project.
- MONTHLY RECURRING FEES




